
Get Ready For the Deprecation of Microsoft Basic Authentication
By Mike Rousos. Authentication is the process of determining a user's identity. Authorization is the process of determining whether a user has access to a resource. In ASP.NET Core, authentication is handled by the authentication service, IAuthenticationService, which is used by authentication middleware.The authentication service uses registered authentication handlers to complete.
.png)
What is MFA and How Can It Protect Your Practice?
4. Top user authentication methods. In order for a user to confirm their identity, the individual must provide a piece of information that only the user and the server knows. Even within each of these types of authentication factors, there are several different methods involved. To simplify things, the way users can verify their identity can be.

Implementing user authentication Maxxton
Authentication is the process of verifying a user's identity through various methods such as passwords, biometrics, and phone/text confirmations. Authentication plays an important role in cybersecurity by protecting sensitive data and maintaining trust through strong authentication measures like MFA (multi-factor authentication).

Types Of Authentication Methods Optimal Idm Gambaran
Authentication is the verification of a user's identity based on their claims. For instance, on a website, users are categorized as Admin or Customer. When a user logs in as an admin, the app checks if they are indeed an admin for successful authentication, and the same process applies to customers. In essence, authentication confirms a user.
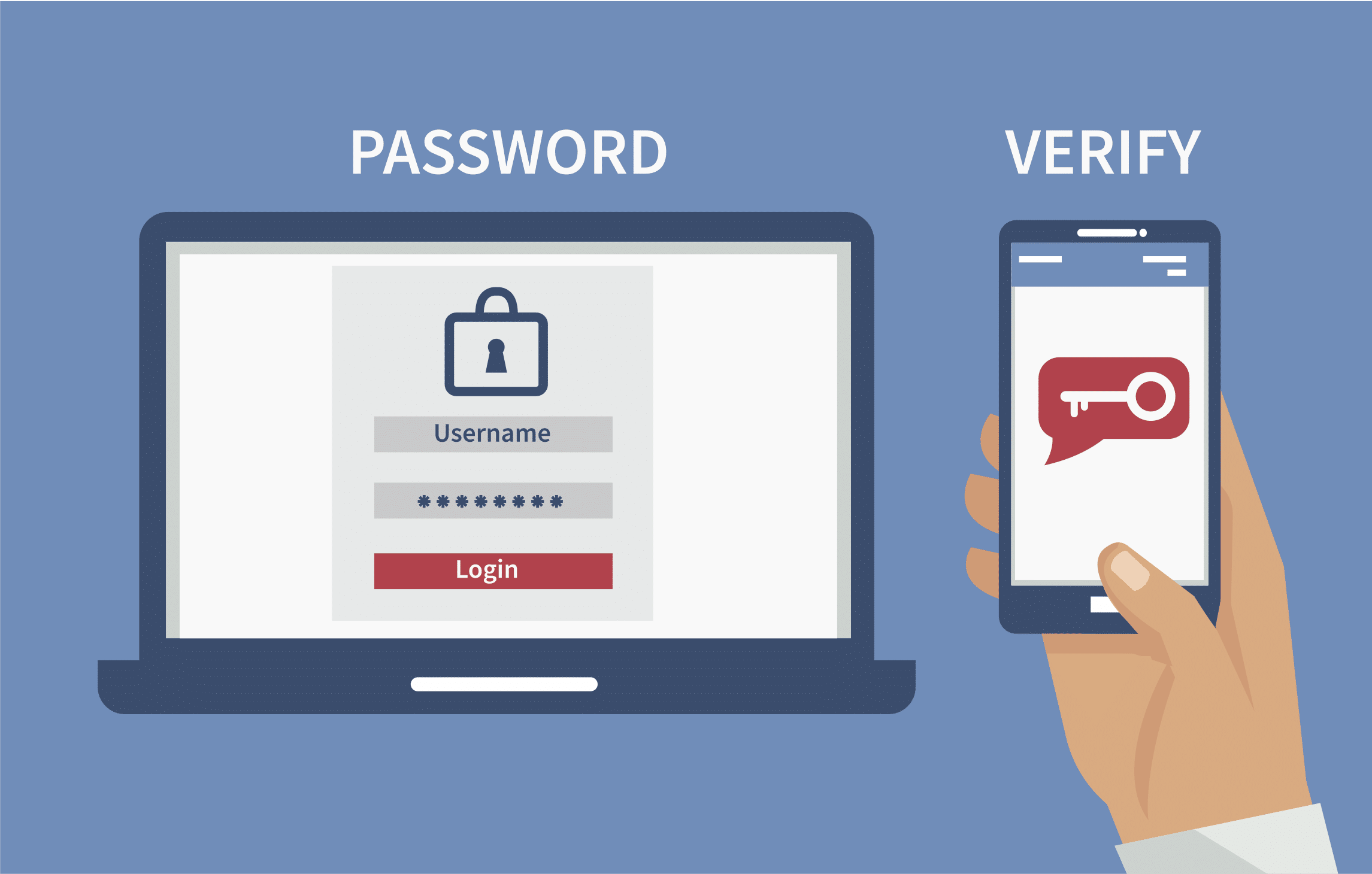
What is Multifactor Authentication? MFA for IT Security
User authentication is the verification of an active human-to-machine transfer of credentials required for confirmation of a user's authenticity; the term contrasts with machine authentication , which involves automated processes that do not require user input.
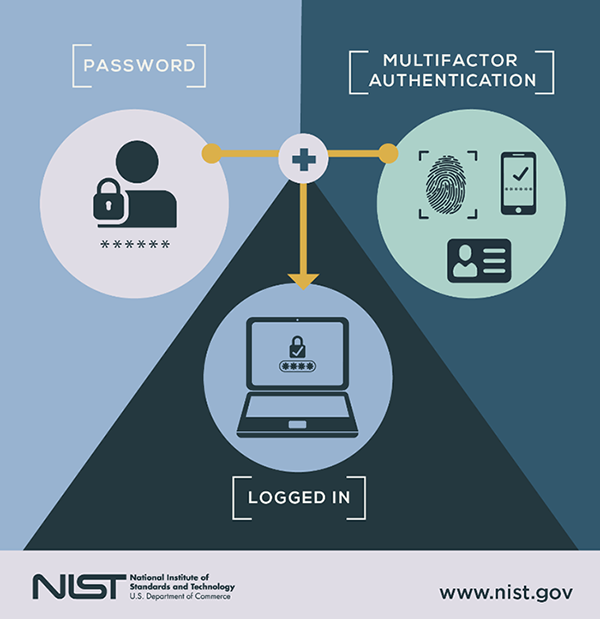
Successful Authentication Management NICE Actimize
User authentication is the process of verifying that users are who they claim to be. It is a crucial part of cybersecurity, enabling organizations to control access to systems and data. There are three main types of authentication factors: Something you know - like a password, PIN, or security question.

Why and how to use twofactor authentication?
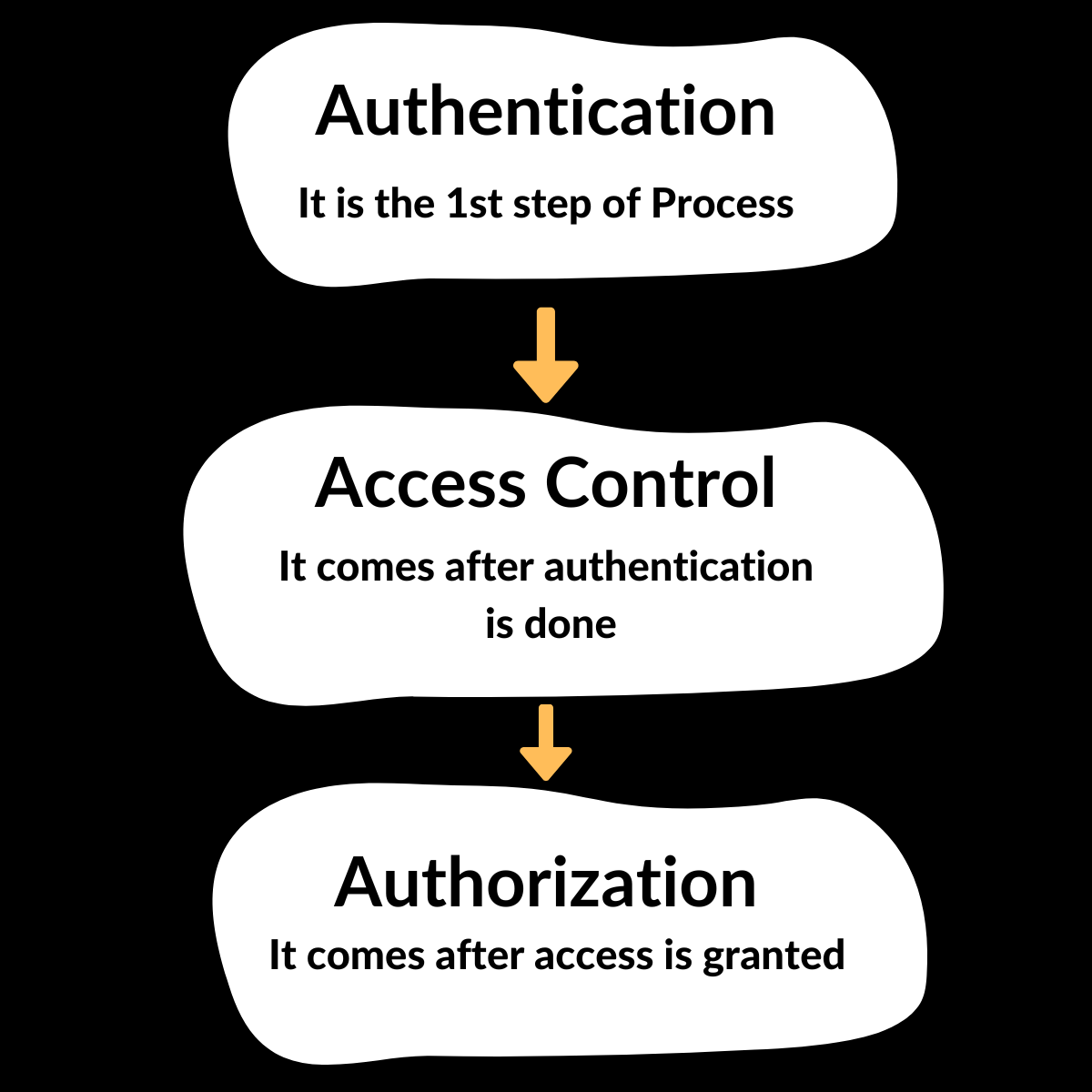
Access control. Authentication proves that you are who you say you are. With this step completed, the server can move through authorization steps and grant access. Cybersecurity. Authentication reduces hacking risks. Sales. Justify a high price for artwork or a collectible by proving that it isn't a forgery. Trust.
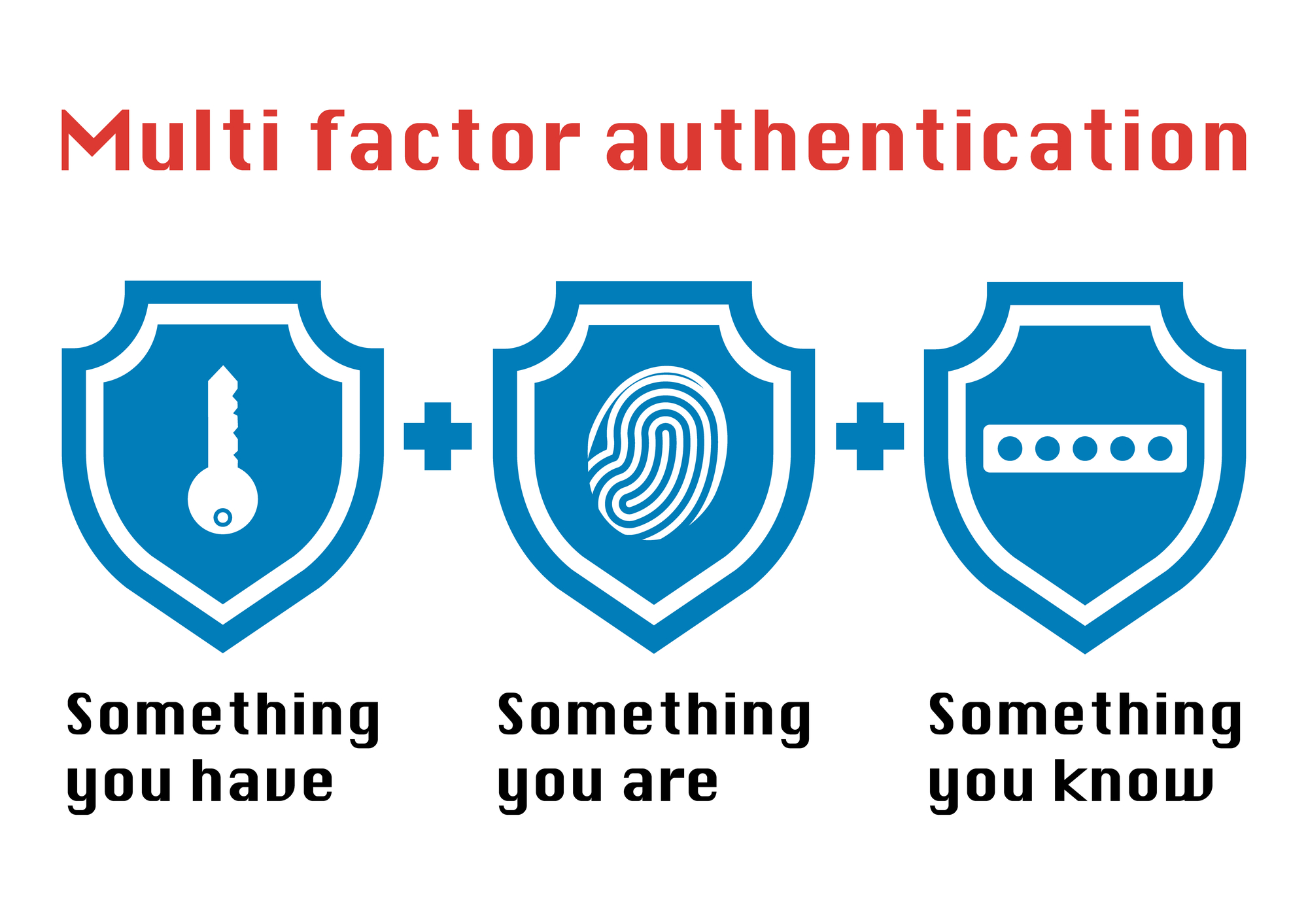
MultiFactor Authentication Basics and How MFA Can Be Hacked PCH
A user authentication policy may be used to help ensure that only the intended audience is accessing certain assets in your organization. User authentication policies strive to ensure that the person requesting sensitive information and data is the right person to access that information.

Two and MultiFactor Authentication for Small Business EIRE Systems
What is authentication? In cyber security, authentication is the process of verifying someone's or something's identity. Authentication usually takes place by checking a password, a hardware token, or some other piece of information that proves identity. Just as an airline worker checks a passport or an identification card to verify a person's.

What to know about user authentication and cyber security
User authentication is important because it helps to protect user accounts, networks, and systems from unauthorized access. Without proper user authentication, threat actors may gain access and compromise both private and business accounts. A breach of one account may easily lead to a breach of all the connected accounts, compromising the user.
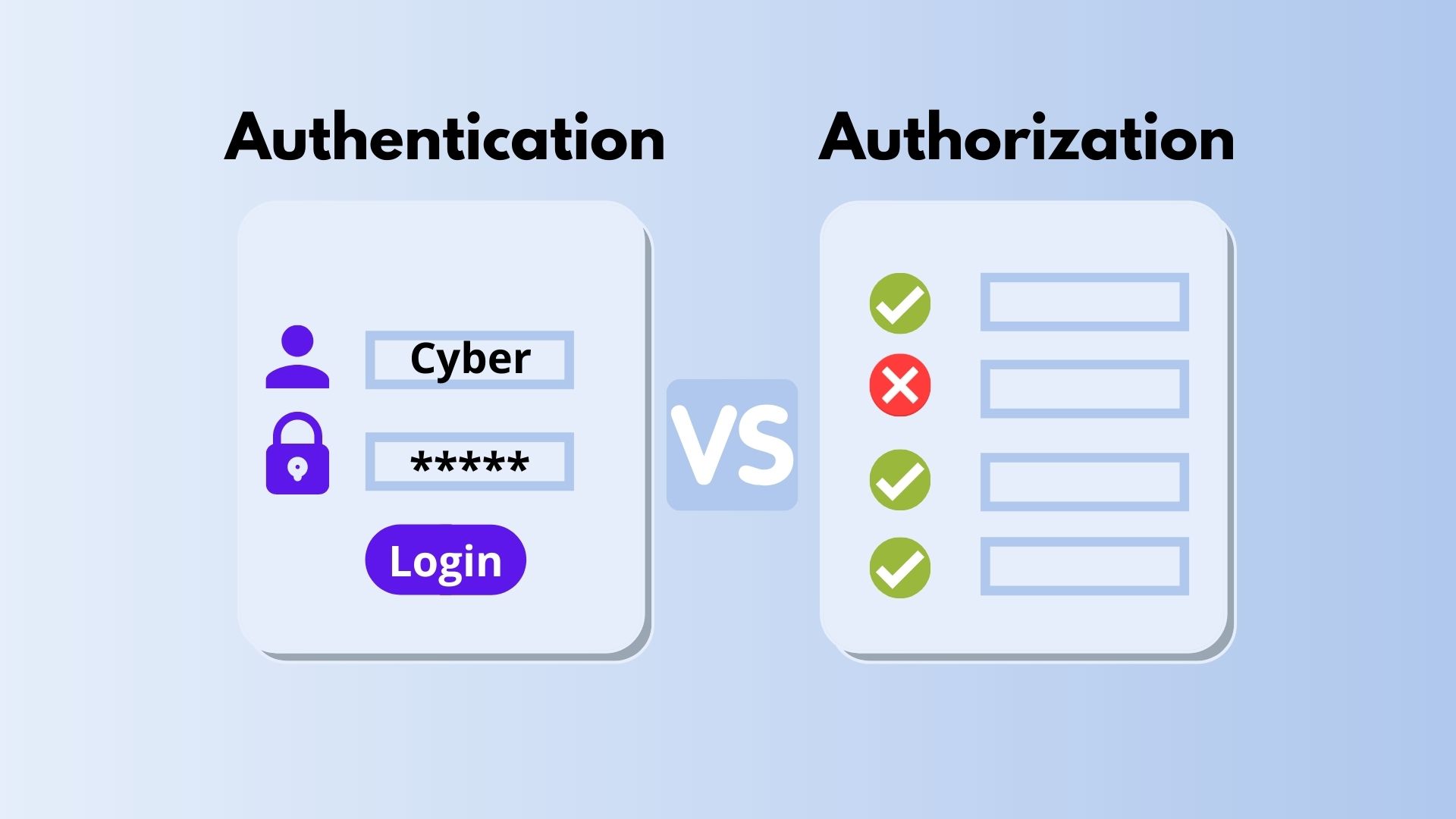
Authentication And Authorization What Comes First In Security
Some user authentication types are less secure than others, but too much friction during authentication can lead to poor employee practices. 6 user authentication types. Authentication methods include something users know, something users have and something users are. Not every authentication type is created equal to protect the network.
Comprehensive Guide to User Authentication Everything you should know
Authentication is the process of confirming that a user is who that person claims to be. An authentication protocol is the method you use to accomplish that task. Several authentication protocols exist. None are 100 percent foolproof. Choose your method carefully, however, and you will reduce the risk of hacking and data theft.

Security Platform
Authentication is a term that refers to the process of proving that some fact or some document is genuine. In computer science, this term is typically associated with proving a user's identity. Usually, a user proves their identity by providing their credentials, that is, an agreed piece of information shared between the user and the system.
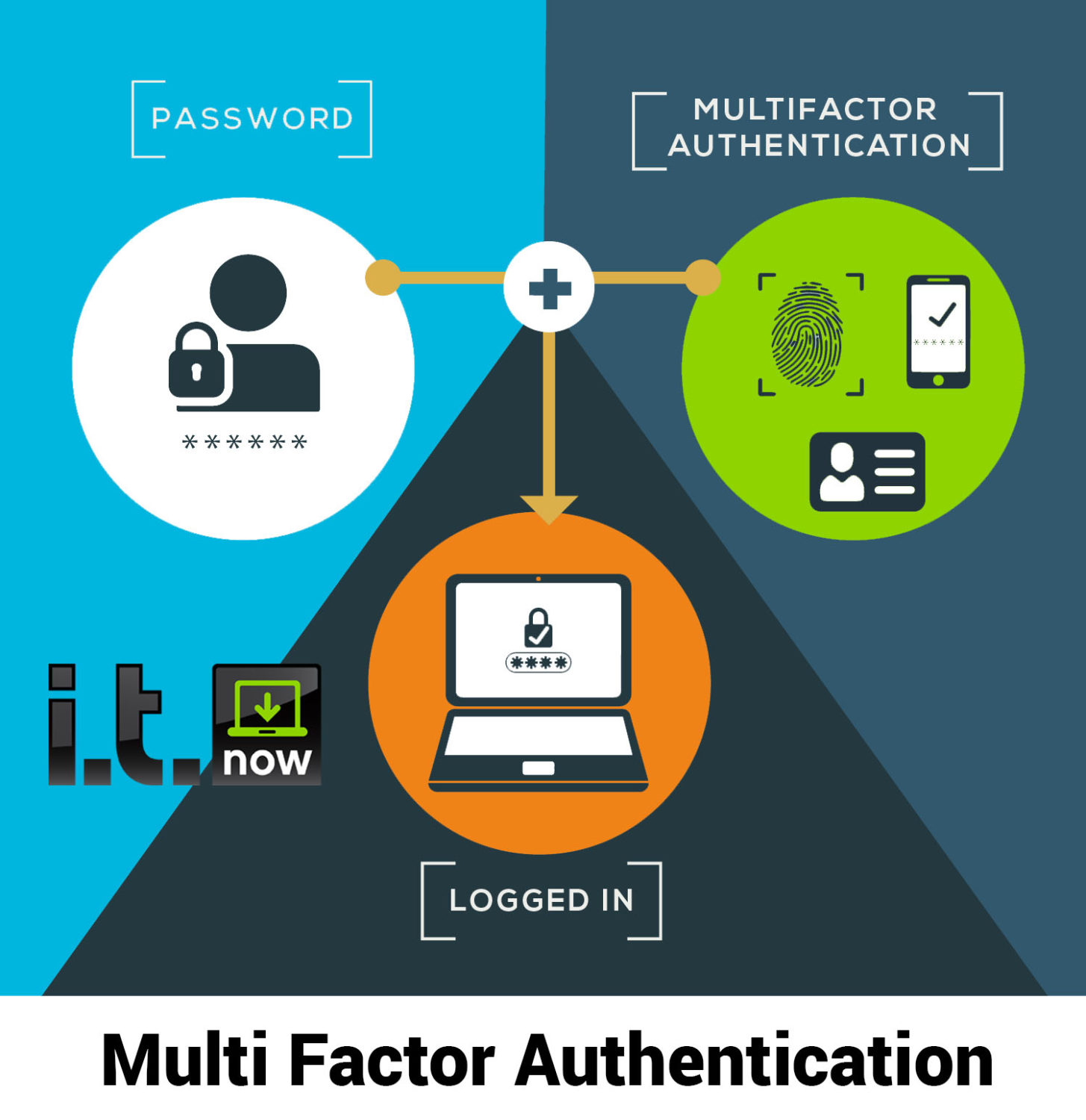
Multi Factor Authentication IT Security Cybersecurity
Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that.

iPhones can now be set up as physical authentication keys TechSpot
Authentication is the process of determining whether someone or something is, in fact, who or what it is declared to be.

Why You Need Advanced Authentication to Protect User Identities
Implementing a secure solution for authentication (signing-in users) and authorization (providing access to secure data) can take significant effort. You must make sure to follow industry best practices and standards, and keep your implementation up to date. The built-in authentication feature for App Service and Azure Functions can save you.