
Configure and manage your mikrotik security best practice by Anu_diu
To show default configuration on your router : /system default-configuration print And if you need to export it : /system default-configuration print file=defconf.txt. MikroTik Security : Built-in Default Configuration "Learn like Newbie, work like Pro" - LucuBRB

Mikrotik Manual Configuration
To set up your security profile, you need to create a new one. Log on to your router via Winbox, click on the wireless tab in the main menu, and double click on the wireless interface you want to configure the security profile on.
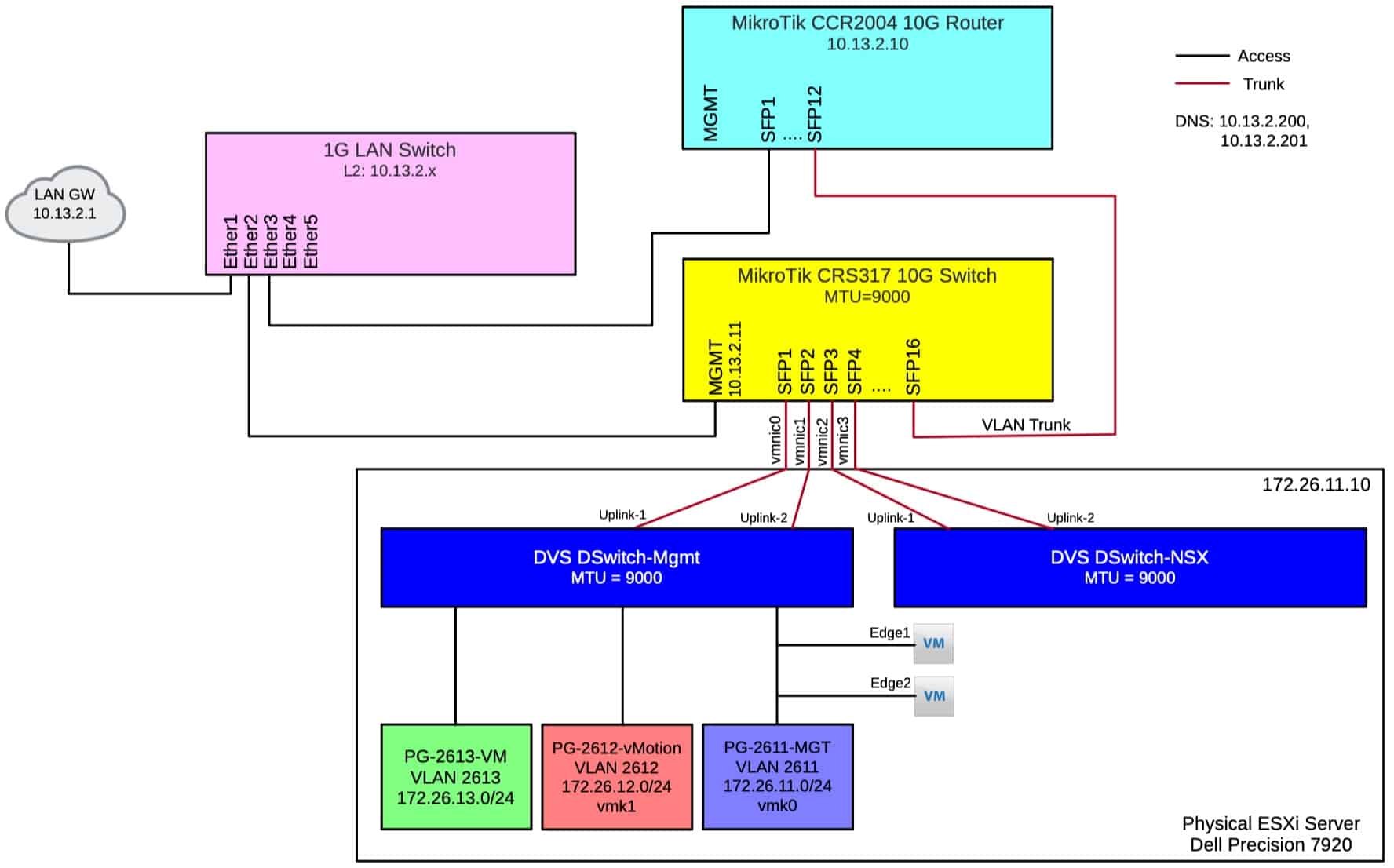
Home Lab MikroTik CCR2004 and CRS317 Configuration Derek Seaman's
Security is big concern for any network device now. In this video you will learn how to secure your mikrotik router in 7 steps. It is very important to secur.
Mikrotik CAPsMAN is Awesome (Home Automation) — Kaspars Dambis
It defintily is not. However, the basic configuration is set to fit the needs of most users. Still, some hardening steps must be taken to increase the security of your Mikrotik server by following the below steps. NMAP: Port and Service scanning

Protecting MikroTik. How to make your router safe HackMag
1 Summary 2 Connecting wires 3 Configuring router 3.1 Logging into the router 3.2 Router user accounts 3.3 Configure access to internet 3.3.1 DHCP Client 3.3.2 Static IP Address 3.3.3 Configuring network address translation (NAT) 3.3.4 Default gateway 3.3.5 Domain name resolution 3.3.6 SNTP Client 3.4 Setting up Wireless

MikroTik WiFi Configuration Simple Setup ShellHacks
Yes! The first step is to back up your Mikrotik device and copy the backup to a safe location. This action is common sense before making any changes to a device or the network. Mikrotik's new BACKUP documentation provides details. (https://help.mikrotik.com/docs/display/ROS/Backup) Don't depend on the Mikrotik Cloud Backup!

MikroTik Wireless Security configuration MikroTik Tips & Tricks
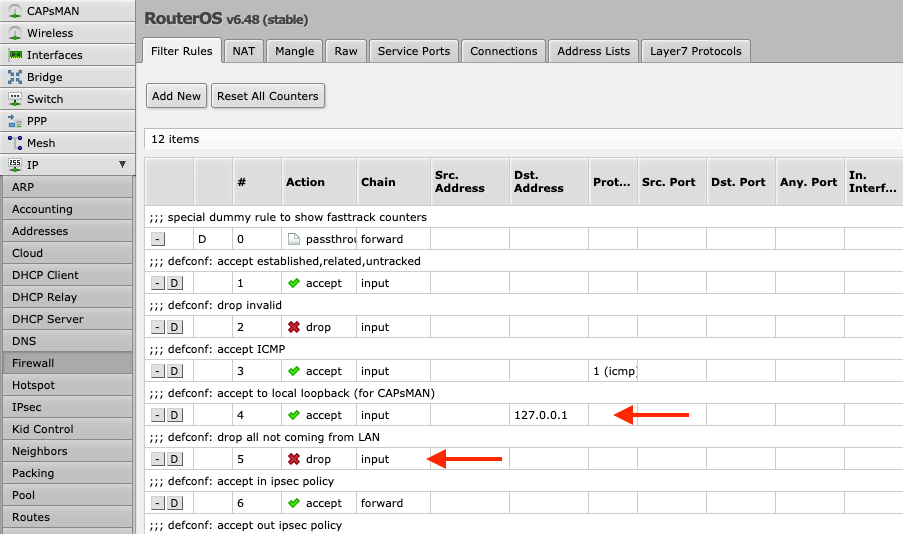
3 Router services 3.1 RouterOS services 3.2 RouterOS MAC-access 3.2.1 MAC-Telnet 3.2.2 MAC-Winbox 3.2.3 MAC-Ping 3.3 Neighbor Discovery 3.4 Bandwidth server 3.5 DNS cache 3.6 Other clients services 3.7 More Secure SSH access 4 Router interface 4.1 Ethernet/SFP interfaces 4.2 LCD 5 Firewall 5.1 IPv4 firewall to a router 5.2 IPv4 firewall for clients
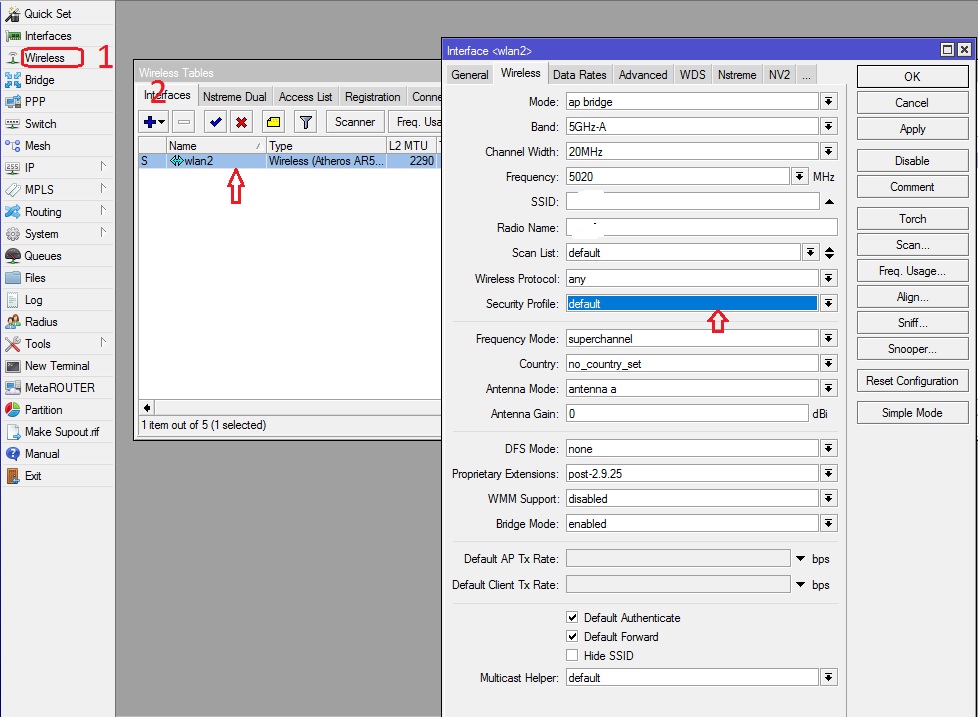
How to create a security profile in Mikrotik Timigate
Overview This article describes a set of commands used for configuration management. Configuration Undo and Redo Any action done in GUI or any command executed from the CLI is recorded in /system history . You can undo or redo any action by running undo or redo commands from the CLI or by clicking on Undo, and Redo buttons from the GUI.

How to configure mikrotik from zero config Tutorial YouTube
#Mikrotik Configuration#Security Guideline. #Mikrotik #protection. Guideline for Mikrotik Configuration. Step0 [0 means do it immediately] /system package update check-for-updates /system routerboard upgrade. Step1(set complex password with special character and disable default admin user).
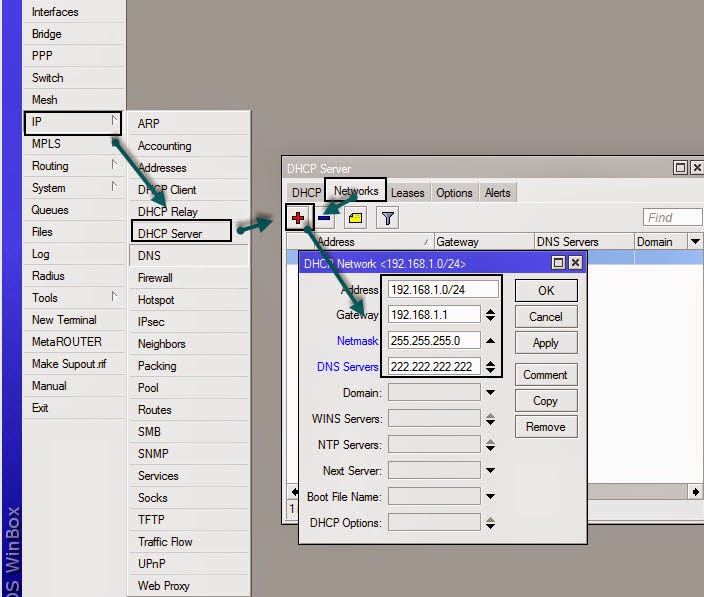
How configure DHCP on MikroTik How2Doc
Re: CAPsMAN on v7.13 configuration. When using VLAN's, you can't use datapath (yet) on AC devices. Hopefully this will be resolved in newer versions of RouterOS, up till then you can use this "hack": The "hack" is using VLAN filtering (manually) on the CAP.
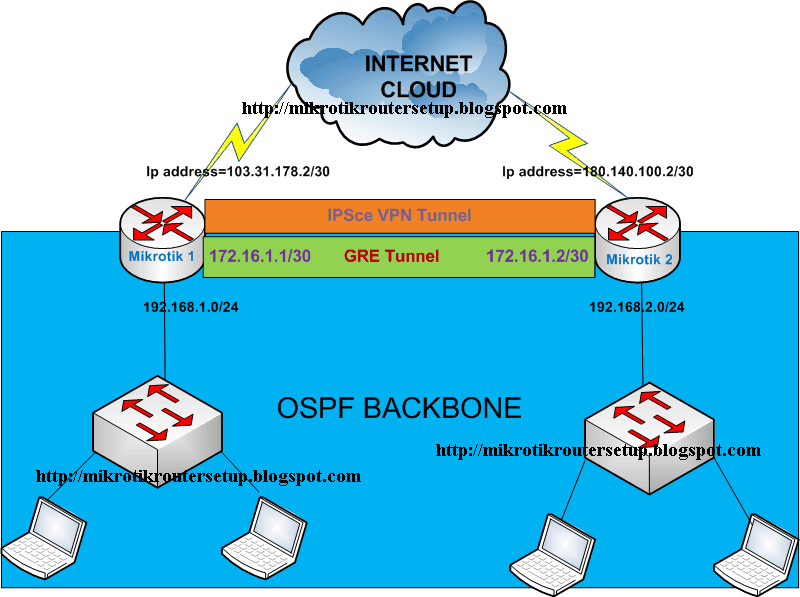
Mikrotik2BRouters2BSite2Bto2BSite2BGRE2Bover2BIPSec2BVPN
Securing RouterOS router. EASY GUIDELINE TO PROTECT YOUR MIKROTIK ROUTEROS ROUTER. Anuwat Ngowchieng. อนุวัตร โง้วเชียง. Consulting Engineer. Internet Thailand Public Company Limited (INET) [email protected]. Certificate: MikroTik: MCTNA, MTCWE Microsoft: MCP, MCSA, MCSE. VMWare: VCP5-DCV.

Static IP Configuration on Mikrotik ( Terminal)
I. Configure security mode. Mikrotik wireless router allows to create separate types of security profiles, which will be imposed in the wireless card configuration section. Go to Wireless -> Security Profiles click Add New. Configuring security profiles has many configuration options depending on the intended use, the following information can.

Mikrotik Network Layout using Mikrotik & Firewall Powered by Kayako
Build real networks while studying for Network+. Hardening steps for securing your MikroTik RouterOS devices. Includes user management, firewalls, IP services, and more.
How to Configure Mikrotik Using CLI Line Interface
Step-by-step guide. Change default user name: Go to System>Users; Click on + to add a new user ; Insert name and set access rights in Group: full; Type in your secure password; Click OK and enable user; Disable default user: admin. Close the Winbox and login with your new username.
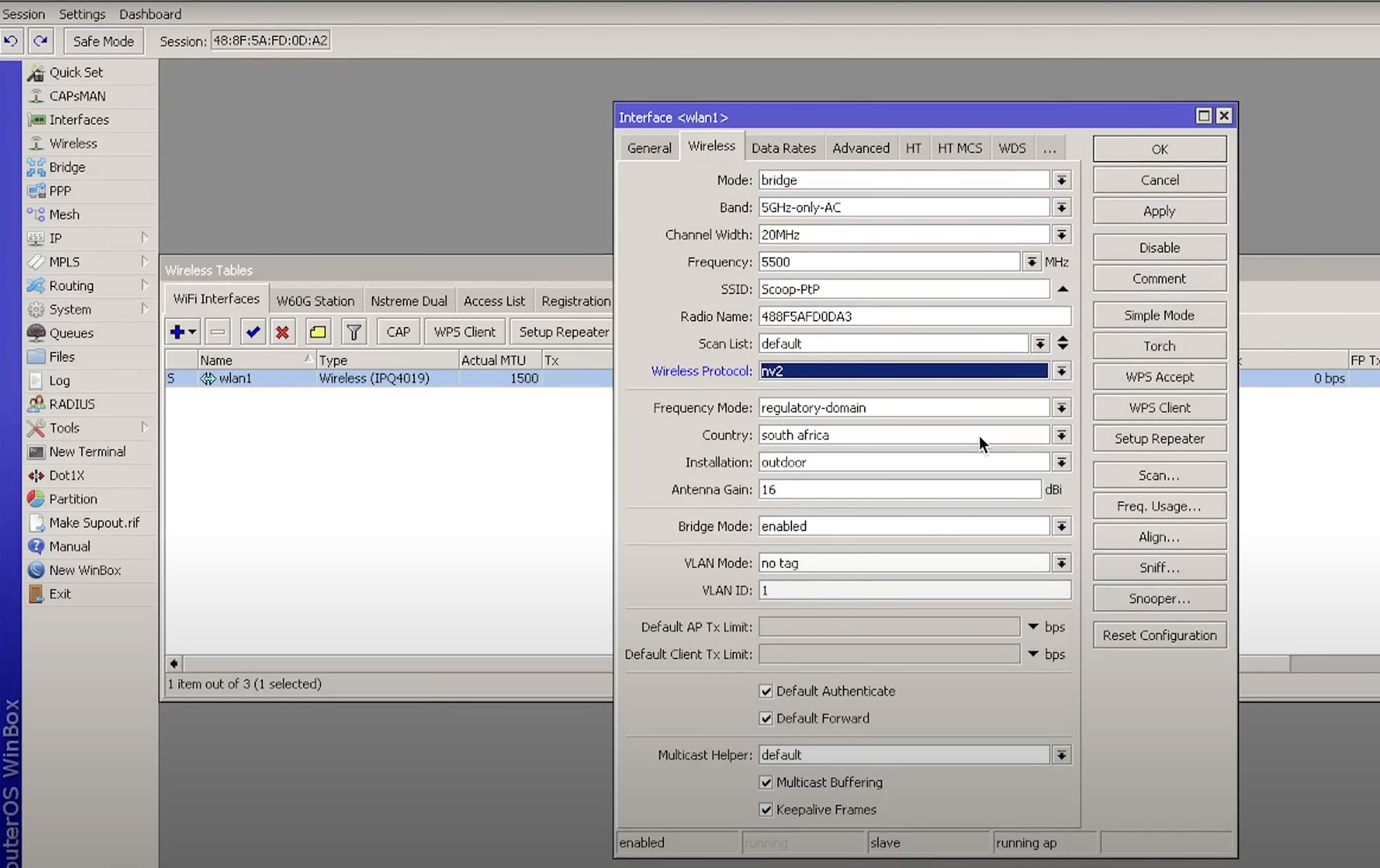
How to Create a MikroTik PtP Bridge Link Scoop
#Mikrotik Firewall #Access Restrictions#How to Secure Your Device from Hacker#Winbox port change#Security of input,output,forward rules Setup With MikroTik#P.
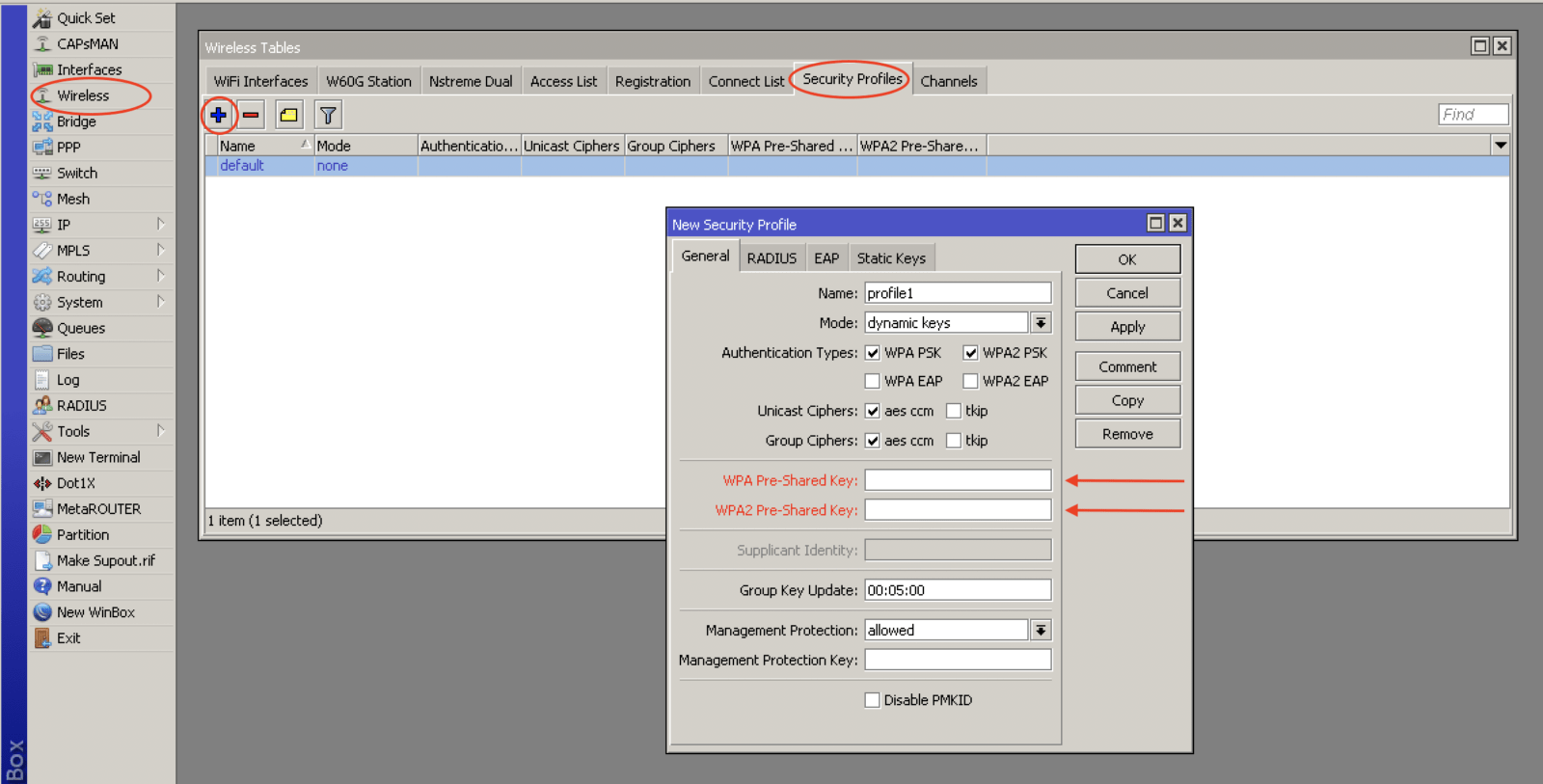
Mikrotik_security_profile Global Hotspot
MikroTik consultant since 2015. [NewUser@MikroTik] > /interface wireless security-profiles \. this default configuration, or you can view them later with '/system default-configuration print' command. To remove this default configuration type "r" or hit any other key to continue.