
Phishing simulation reveals 70 of workers who clicked on malicious link
Understand the security, performance, technology, and network details of a URL with a publicly shareable report. Scan. URL Scanner Terms. Additional settings.

Download Link Phising FB [Script Phising Gratis] 2022 AC10
Check suspicious links with the IPQS malicious URL scanner.Real-time results detect phishing links and malware domains with accurate, deep machine learning analysis. Check URLs for phishing, malware, viruses, abuse, or reputation issues. Use this free URL scanner to prevent suspicious links, scams, or dangerous websites. Scan user generated content, email messages, and page links with reliable.

What Is Phishing And How It Affects A Business Sectigo® Official
Last Update: 2023-10-11. Download. Summary. Files. Reviews. King Phisher is an open source tool that can simulate real world phishing attacks. It has an easy-to-use, flexible architecture that allows for full control over both emails and server content. It is useful for running awareness campaigns and training, and can only be used for legal.
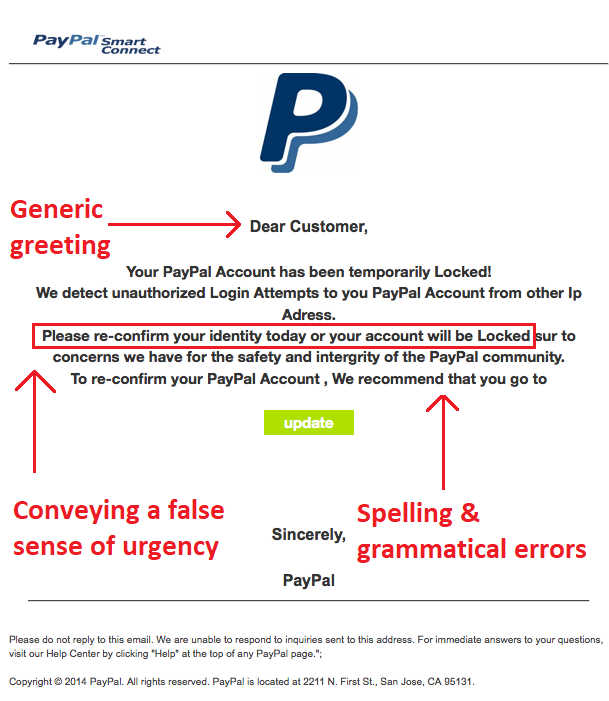
Was tun, wenn Sie auf einen PhishingLink klicken 4 Schritte zur
Meet the Author Emily Jones, PMP, CMMC-RP. Emily Jones serves as the Principal Practice Leader for Warren Averett Technology Group. She has more than 30 years of experience, including a 12-year career at NCR Corporation, a world leader in transaction technologies, and 20 years with Jackson Thornton Accounting and Consulting in their technology group where she was a founding member.

What Happens if You Click on a Phishing Link? EasyDMARC
The phishing site is now fully active. To download the phishing kit, you'll need to strike in the short window between the kit being uploaded and it being deleted again. This is usually only a matter of minutes! But actually, downloading the kit is often the easy part. The tricky part is finding a phishing domain before it's been set up.

How to detect a phishing URL using Python and Machine Learning
Phishing is a form of social engineering in which an attacker masquerades as a trustworthy entity and tries to persuade, scare, or threaten the recipient to take a specific action or reveal personal information that leads to a security compromise. Phishing attacks use email, text messages, social media posts, voice communications, and other media.
What Should You Do When You Receive a Phishing Email? Ophtek
Publisher Name Springer, Cham. Print ISBN 978-3-031-23159-9. Online ISBN 978-3-031-23161-2. 'Anti-phishing Attacks in Gamification' published in 'Encyclopedia of Computer Graphics and Games'.

How to Check a Link for Phishing EasyDMARC
Close the tab. Visit the real site using a URL you know or a bookmark you've previously saved. Change your password. Review your account recovery information. If you can't sign in, the hacker behind the (now successful) phishing email may have already changed your password. If so, your account has been hacked.
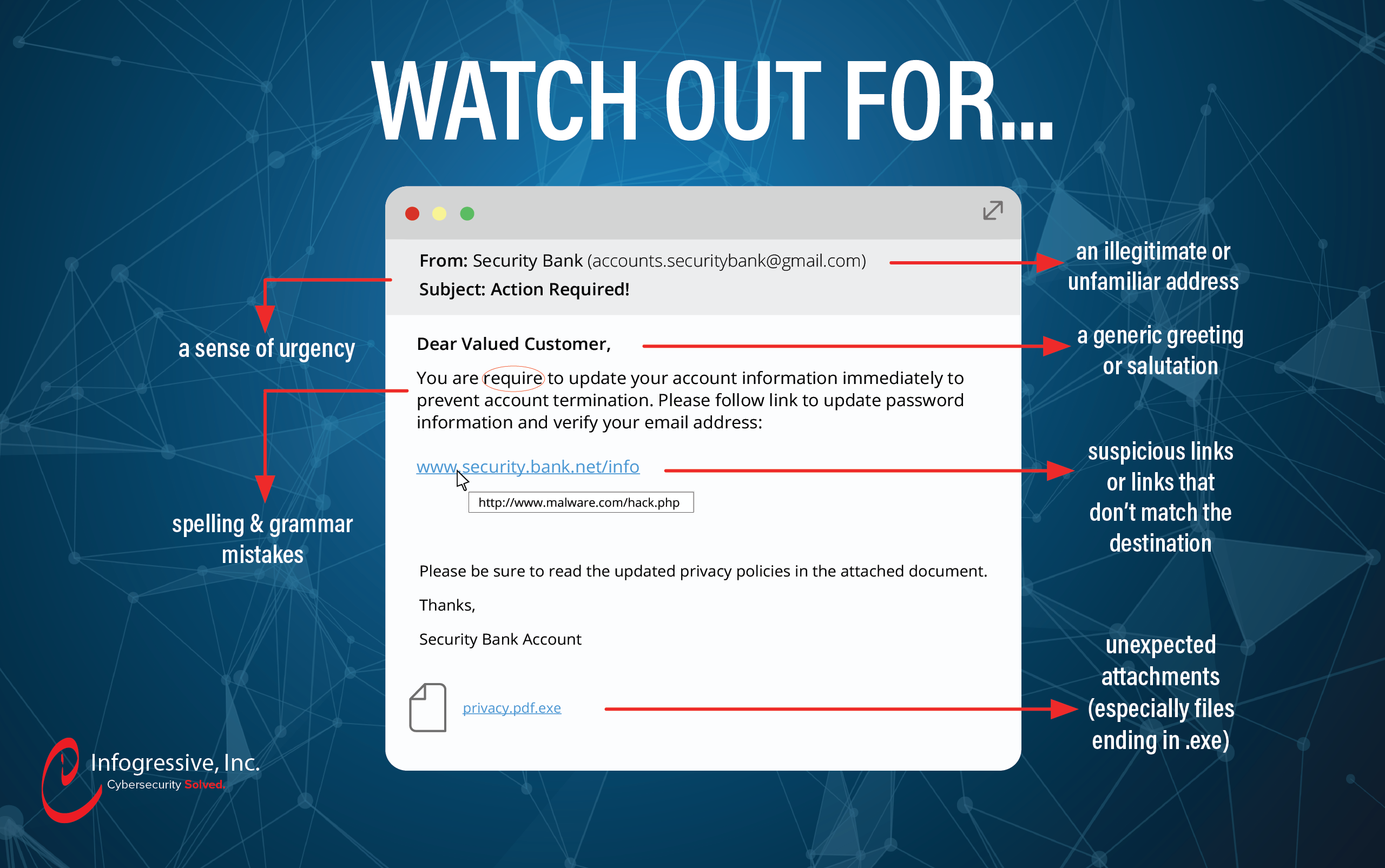
Analysis of a DocuSign Phishing Email
Google Inc. 03:07:07. Download Free Phishing Feed. OpenPhish provides actionable intelligence data on active phishing threats.
Download Link Phising FB 2023 CaraTrend
Open-Source Phishing Framework. Gophish is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing. For free.

What To Do If You Click On A Phishing Link 2021 Guide
After clicking a phishing link, the sender knows you are a valid target. The attacker receives basic data like approximate location, device statistics, and any information voluntarily provided. A phishing link may download malware. Users should take precautionary measures. So if the sender gets this information, what are the immediate risks to.

50+ Phishing Email Examples Common Types and Examples of Phishing
Protect yourself from phishing. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Cybercriminals typically pretend to be reputable companies.
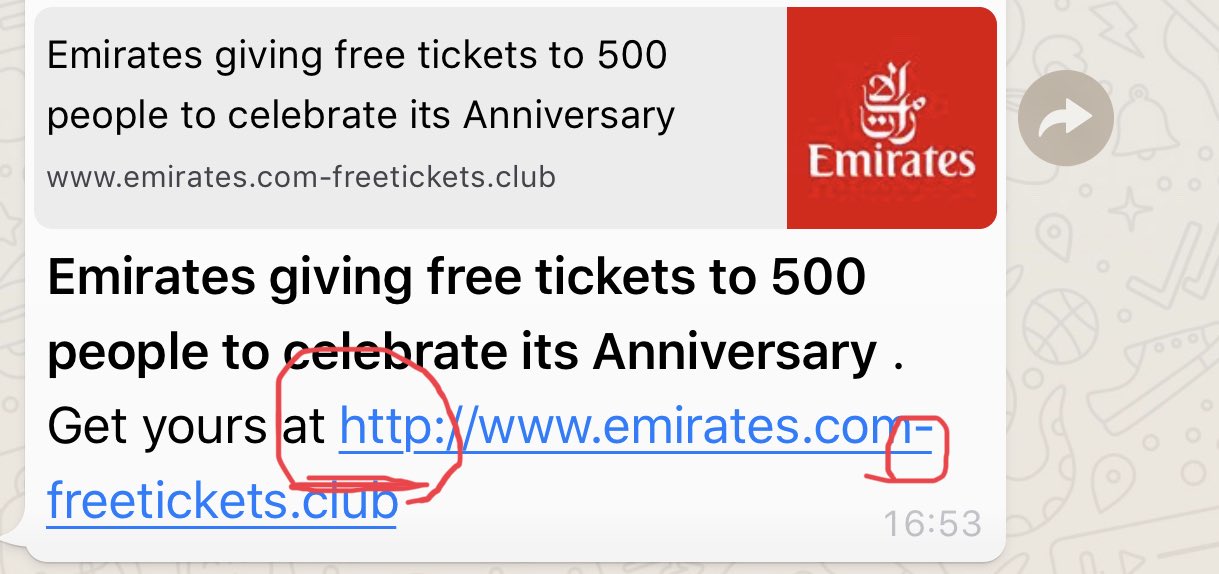
A Few Tips to Detect Phishing Links SMEX
A new variant of a remote access trojan called Bandook has been observed being propagated via phishing attacks with an aim to infiltrate Windows machines, underscoring the continuous evolution of the malware.. Fortinet FortiGuard Labs, which identified the activity in October 2023, said the malware is distributed via a PDF file that embeds a link to a password-protected .7z archive.

Top 5 Most Common Phishing Attacks » The Merkle News
A phishing attack is an attempt by criminals to trick you into sharing information or taking an action that gives them access to your accounts, your computer, or even your network. It's no coincidence the name of these kinds of attacks sounds like fishing. The attack will lure you in, using some kind of bait to fool you into making a mistake.
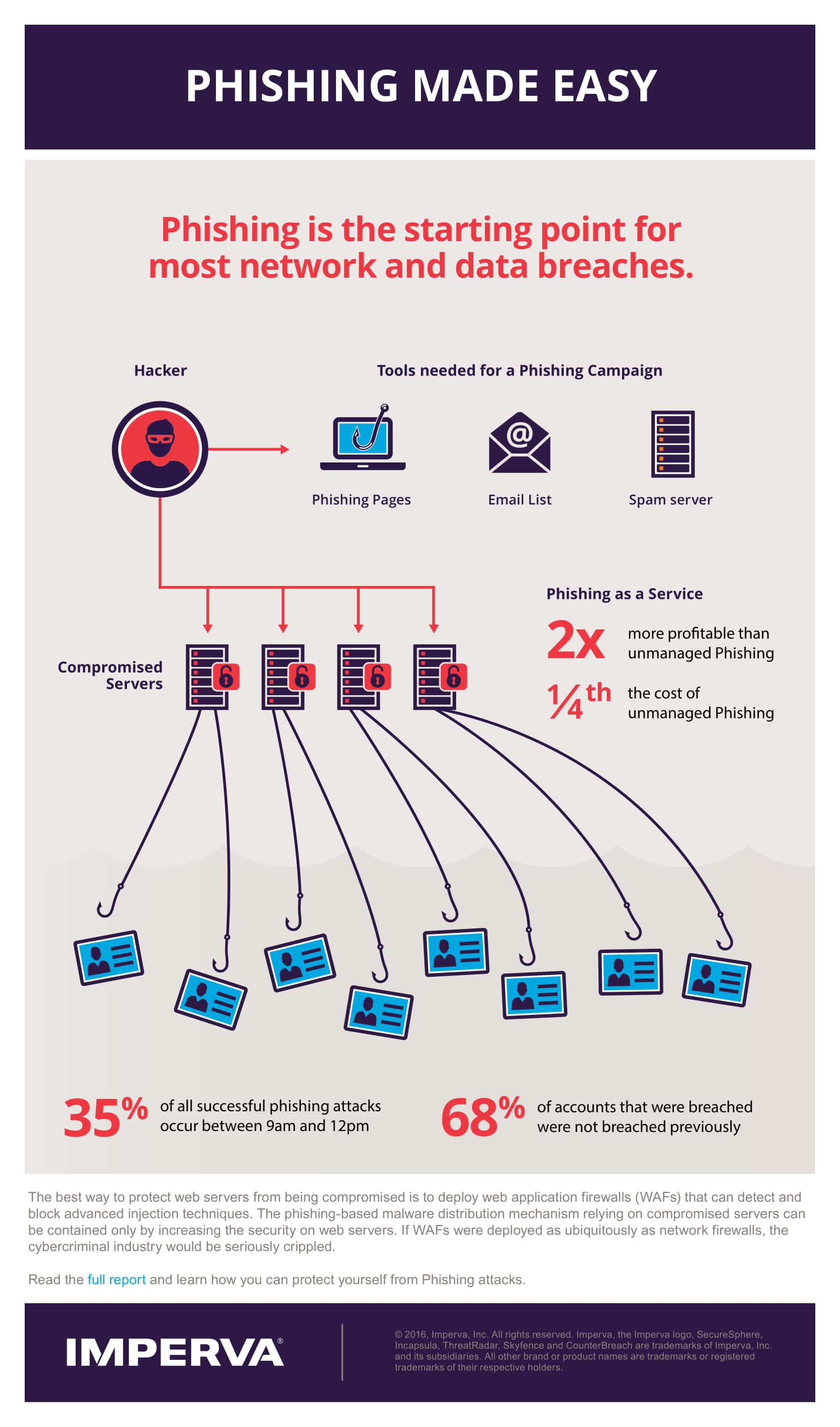
Get Your Infographic
3 Steps To Take if You've Clicked on a Phishing Link. If you click on a phishing link here are three steps you need to take. 1. Disconnect your device from the internet. The very first step you should take after discovering you've clicked on a phishing link is to disconnect your device from the internet.

How to Purify Your Device After Clicking a Phishing Link
Spear Phishing. Spear phishing is a targeted form of phishing where attackers tailor messages to specific individuals or organizations, using collected data to make the deceit more convincing. It requires pre-attack reconnaissance to uncover names, job titles, email addresses, and the like.